What is AWS CloudFront or Amazon CloudFront
Amazon CloudFront
Amazon CloudFront is a fast content delivery network (CDN) service that safely delivers data, videos, applications, and APIs to clients internationally with low latency, high transfer speeds, all within a developer-friendly environment. CloudFront is integrated with AWS – both physical areas that are legitimately connected with the AWS global infrastructure, just as other AWS services. CloudFront works flawlessly with services including AWS Shield for DDoS mitigation, Amazon S3, Elastic Load Balancing, or Amazon EC2 as origins for your applications, and Lambda@Edge to run custom code nearer to the clients and to modify the user experience. In conclusion, on the off chance that you use AWS roots, for example, Amazon S3, Amazon EC2, or Elastic Load Balancing, you don't pay for any data moved between these services and CloudFront.
You can begin with the Content Delivery Network in minutes, utilizing the same AWS tools that you're already familiar with: APIs, AWS Management Console, AWS CloudFormation, CLIs, and SDKs. Amazon's CDN offers a straightforward, pay-as-you-go pricing model with no upfront charges or required long-term contracts, and backing for the CDN is included in your current AWS Support subscription.
Key Features
Amazon CloudFront Infrastructure
The Amazon CloudFront Global Edge Network
To deliver content to end clients with lower latency, Amazon CloudFront uses a global network of 216 Points of Presence (205 Edge Locations and 11 Regional Edge Caches) in 84 cities across 42 nations. Amazon CloudFront Edge areas are situated in: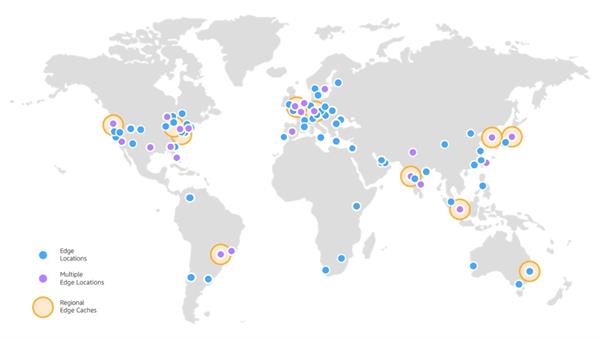
Security
Protection against Network and Application Layer Attacks
Amazon CloudFront, AWS Shield, AWS Web Application Firewall (WAF), and Amazon Route 53 work flawlessly together to make a flexible, layered security perimeter against different sorts of attacks including network and application layer DDoS attacks. All of these services are co-resident at the AWS edge and give a versatile, reliable, and high-performance security perimeter for your applications and content. With CloudFront as the "front door" to your application and framework, you are moving the primary attack surface away from your critical content, data, code, and infrastructure.
SSL/TLS Encryption and HTTPS
With Amazon CloudFront, you can deliver your content, APIs, or applications by means of SSL/TLS, and advanced SSL features are enabled automatically. You can use AWS Certificate Manager (ACM) to easily make a custom SSL certificate and deploy it to your CloudFront circulation for free. ACM consequently handles certificate renewal, excluding the overhead and expenses of a manual renewal process. Furthermore, CloudFront gives various SSL optimizations and advanced capabilities like full/half bridge HTTPS connections, OCSP stapling, Session Tickets, Perfect Forward Secrecy, TLS Protocol Enforcements and Field-Level Encryption.
Access Control
With Amazon CloudFront, you can limit access to your content through various capabilities. With Signed URLs and Signed Cookies, you can support Token Authentication to confine access to just authenticated viewers. Through geo-restriction capability, you can keep clients in explicit geographic areas from accessing content that you're distributing through CloudFront. With Origin Access Identity (OAI) feature, you can confine access to an Amazon S3 bucket to just be accessible from CloudFront.
Compliance
CloudFront infrastructure and processes are all compliant with PCI-DSS Level 1, HIPAA, and ISO 9001, ISO 27001, SOC (1, 2, and 3) to ensure the secure delivery of your most sensitive data.
Availability
Increase application availability
Web applications frequently need to fight with spikes in traffic during peak periods of activity. By using Amazon CloudFront, you can cache your content in CloudFront's edge locations worldwide and decrease the remaining workload at hand on your origin by only fetching content from your origin when required. This diminished outstanding workload on your origin helps you increase the availability of your application.
Enabling redundancy for origins
CloudFront additionally permits you to set up different origins to enable redundancy in your backend infrastructure. You can use CloudFront's native origin failover capability to consequently serve your content from a backup origin when your primary origin is not accessible. The origins that you set up with origin failover can be any combination of AWS origin points like EC2 instances, Amazon S3 buckets, or Media Services, or non-AWS origins like an on-premises HTTP server.
Performance
Network optimization for optimal performance
Amazon CloudFront is persistently measuring internet connectivity, performance, and computing to locate the most ideal approach to route requests to our network; considering performance, load, operational status, and different variables to convey the best experience in real-time. Amazon CloudFront is additionally running on the AWS global network backbone, that takes into consideration efficient transmission of requests between the CloudFront Edge locations and other AWS services, across regions and applications. Network-layer optimizations, for instance, TCP fast open, request collapsing, keep-alive connections, and much more, empower the Amazon CDN to accelerate both static and dynamic content for improved client performance.
Large libraries and media assets
As the global network infrastructure has developed and improved, cache retention has emerged as a key supporter of performance. The content delivery network (CDN) is designed to keep objects longer in the cache and to diminish the cache churn. Procedures like tired caching and de-duplication optimization of objects in cache reserve help expand cache retention.
Programmable and DevOps Friendly
Full-featured APIs and DevOps Tools
Amazon CloudFront gives developers a full-featured API to make, configure, and maintain your CloudFront dispersions. Furthermore, developers approach various tools like AWS CloudFormation, CodeDeploy, CodeCommit, and AWS SDKs to configure and deploy their remaining workload at hand with Amazon CloudFront.
Lambda@Edge
Lambda@Edge helps web developers, mobile developers, and Amazon CloudFront clients run their code closer to their clients. Using Lambda@Edge permits you to respond to requests at the lowest latency across AWS locations internationally. For web or mobile requests, the compute request from your clients can be delivered closer to them, improving their overall experience. You pay just for the computing time you use. There is no charge when your code isn't running.
Cost-Effective
Pay-as-you-go publically available pricing and committed-traffic private pricing
With Amazon CloudFront pay-as-you-go pricing, you pay just for what you use. There is no minimum fee. For users who are willing to make certain minimum traffic commitments, they also offer private committed pricing.
Free data Transfer between AWS cloud services and Amazon CloudFront
If you use AWS origins such as Amazon S3, Amazon EC2, or Elastic Load Balancing, you don’t pay for any data transferred between these services and CloudFront.
How you Set Up CloudFront to Deliver Content
You make a CloudFront distribution to tell CloudFront where you need the content to be delivered from, and the insights concerning how to track and manage content delivery. At that point, CloudFront utilizes computers—edge servers—that are near your viewers to deliver that content immediately when somebody needs to see it or use it.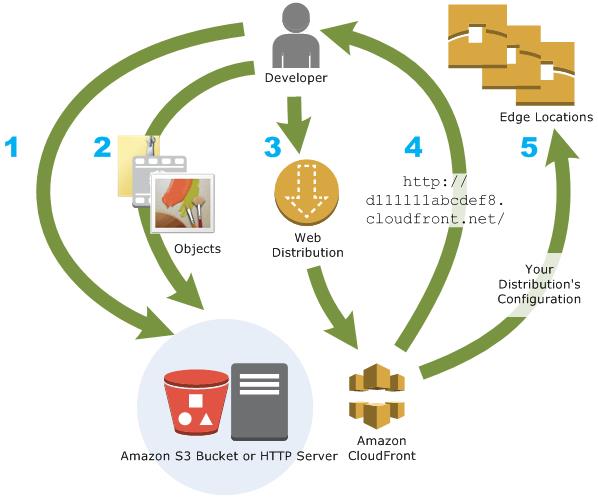
How you configure CloudFront to deliver your content
- You determine origin servers, similar to an Amazon S3 bucket or your own HTTP server, from which CloudFront gets your files which will at that point be scattered from CloudFront edge areas everywhere throughout the world.
A beginning server stores the first, definitive version of your objects. In case you're serving content over HTTP, your source server is either an Amazon S3 bucket or an HTTP server, for example, a web server. Your HTTP server can run on an Amazon Elastic Compute Cloud (Amazon EC2) instance or on a server that you deal with; these servers are otherwise called custom origins.
On the off chance that you use the Adobe Flash Media Server RTMP convention to circulate media files on request, your origin server is consistently an Amazon S3 bucket.
- You upload your files to your origin servers. Your files, otherwise called objects, ordinarily include web pages, images, and media files, yet can be whatever that can be served over HTTP or a supported version of Adobe RTMP, the protocol used by Adobe Flash Media Server.
In case you're using an Amazon S3 bucket as an origin server, you can make the objects in your bucket publically readable so that any individual who knows the CloudFront URLs for your objects can access them. You also have the alternative of keeping objects private and controlling who has access to them.
- You make a CloudFront distribution, which discloses to CloudFront which origin servers to get your files from when clients demand the files through your web site or application. Simultaneously, you indicate details like whether you need CloudFront to log all requests and whether you need the distribution to be enabled as soon as it's created.
- CloudFront assigns a domain name to your new distribution that you can find in the CloudFront console, or that is returned in the reply to a programmatic request, for instance, an API request. Instead, if you like you can add another area name to use.
- CloudFront sends your distribution's configuration (however not your content) to the entire of its edge location or points of presence (POPs)— assortments of servers in geologically scattered data communities where CloudFront stores duplicates of your files.
As you build up your website or application, you use the domain name that CloudFront produces for your URLs. For instance, if CloudFront returns d111111abcdef8.cloudfront.net as the domain name for your distribution, the URL for icon.jpg in your Amazon S3 bucket (or in the root catalog on an HTTP server) is http://d111111abcdef8.cloudfront.net/icon.jpg.
Or on the other hand, you can set up CloudFront to use your own domain name with your distribution. In that case, the URL may be http://www.example.com/icon.jpg.
Alternatively, you can configure your root server to add headers to the files, to demonstrate to what extent you need the files to remain in the cache in CloudFront edge locations. By default, each file remains in an edge location for 24 hours before it expires. The base expiration time is 0 seconds; there isn't a maximum expiration time.